The core of every CmDongle is a smart card chip, which includes a microcontroller with a secure storage area for cryptographic keys and the firmware. How to get a yellow ring around your cursor for mac. Wibu-Systems currently uses smart card chips from Infineon Technologies, which are EAL 5+ evaluated and provide protection against side channel attacks, such as DPA (Differential Power Analysis).
- Go into Device Manager and make note of the COM port used by the adapter. Install the Tis2000 software from the CD included with the Tech2. During the install, it will ask you to specify the COM port. If you have a serial port on the computer, it's probably COM 1 or use the one from the USB adapter.
- How to Install & Activation DS150 Software (Guide Video in Bottom) Del-phi DS15e is the new vci that supports cars and trucks till 2017. The ds150e software can work with several diagnostic tools, such as WOW, CDP, Auto-com, MVDiag tools TCS CDP, etc. V2015.3 ds150e software is already with keygen activator in the software, so VXDAS.COM would like to share the different versions of the ds150.
- Portable storage for the paranoid: We test two secure USB drives on keypad vs. Software security Product Review: Aegis Padlock DT FIPS – USB 3.0 Desktop Drive Review – Aegis Secure Key 3NX Flash Drive and Fortress L3 Padlock.
- Here is how a dongle works; when a programing function starts, it reaches for the dongle to attain the security code to proceed with its operation. Making a duplicate of the Dongle. The most suitable and apt way to replicate a dongle or security key is a software called Dognify. Special software that will let you share the dongle to other networks.
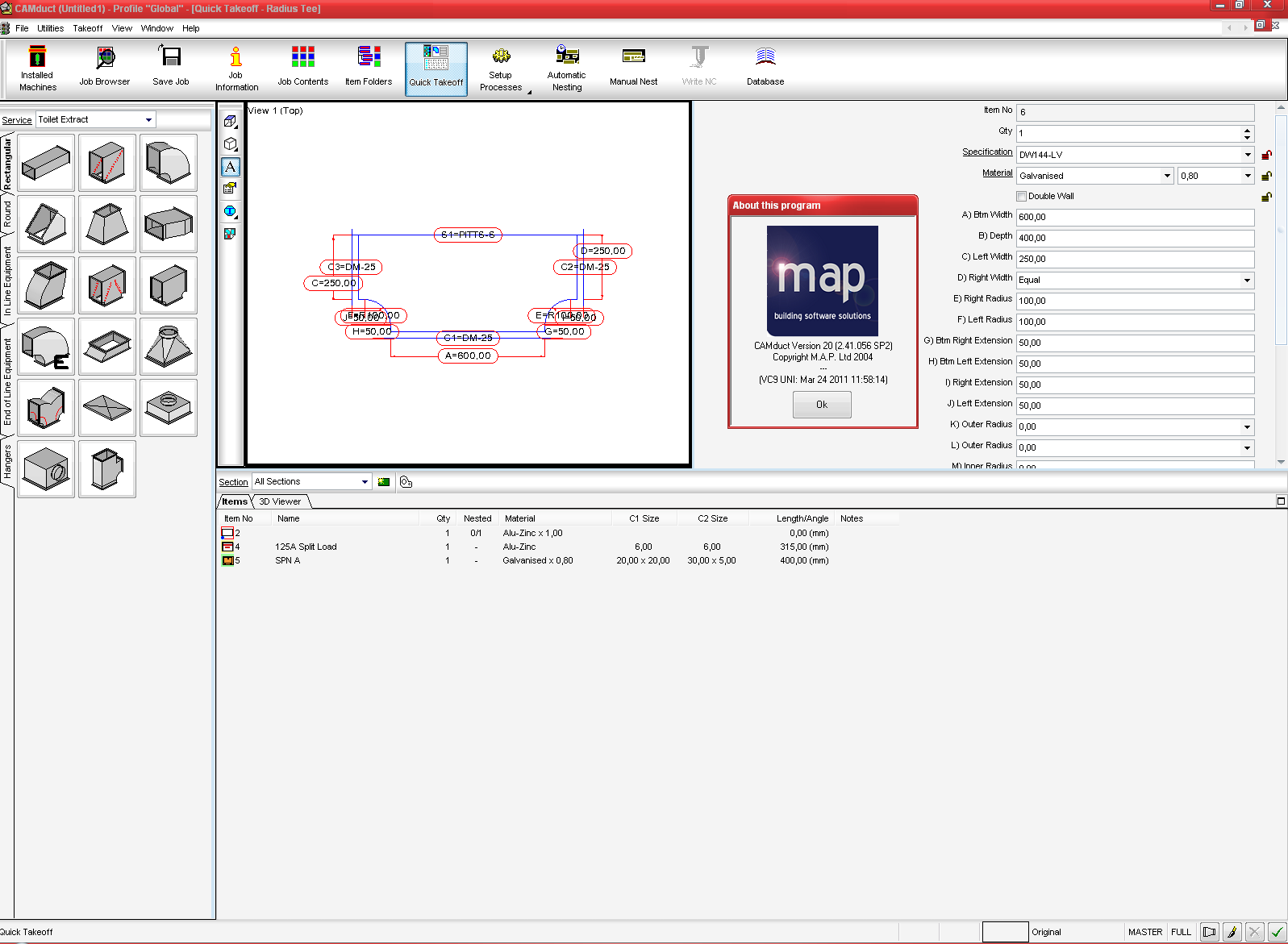
Dongle - is a digital device with the function of software protection against unlicensed use. Dongle contains a programmable memory area. The program at start drawn to this area of memory. If the device is missing, the program does not start or runs in a restricted mode. You can use the device contemporaneously only on a single machine. If used two or more computers, and they are located in different places, protection module will have to be transported from one place to another. This variant of the use of a dongle can cause damage to it or the module may be lost. The user will have again to pay money for the restoration of the module.
The memory of the key usually contains:
- - the expiry date of the license;
- - the name of the owner of the license;
- - the number of activated and prepaid modules;
- - the encrypted part of the program code, which is required to run.
Dongle Clone Software Download Windows
What dongle emulator and what is it needed for?
Dongle Clone Software Download Software
Dongle emulator - is a software equivalent of real module. We create such similar key. It works on all versions of Windows (XP, Vista, 7, 8.1) 32 and 64 bits. Our clients can also get dongle dump - backup the contents of the key. We always offer free dumper dongle. Dump dongle allows us to make the emulator and you can download dongle emulator from us.
How does it work? Windows and protected software product react with dongle emulator just the same if it was a real key. Zio card reader driver for mac. Our emulator has a lot of advantages. We can do dongle crack, i.e. to read the data in memory of this key, and then upgrade content, adding new options. Your key after this modernization has:
- - the new date of license expiration
- - the new name of the license holder
- - the entire set function of software product
Dongle crack - is an emulator with modified memory, while in the emulator memory is taken from the real dongle unchanged.
Cajviewer for mac. Executable files (*.exe), libraries (*.dll), and others we may change by the patch. This method makes it possible to check the presence of key without any the conditions. The key is typically connected to a USB port. We can do dongle crack and thereby to signal a persistent connection security module.

